Article Posted August 17, 2011

Identity and Access Management
"… User accounts must be properly managed, and old and inactive accounts de-provisioned in accordance with policy.”
In multiple audits of identity and access management for USG’s three primary enterprise information technology systems (PeopleSoft, BANNER, and ADP), we found active user accounts associated with employees who had separated from service, and many other old user accounts that were not fully deactivated. All institutions should work to diligently manage access to these systems, and have many options and tools to achieve this goal, including the following recommendations:
- Conduct basic comparisons of active user accounts to the institution’s roll of current employees and identify variances;
- Use existing reports and business processes defined by ITS to regularly analyze user accounts and related permissions; and,
- Ensure a user’s level of access appropriately matches their assigned duties and responsibilities (no more, no less).
This issue is easily remedied for the PeopleSoft system, and several existing business practices designed to assist database and security administrators with provisioning and de-provisioning access currently exist. In our analysis, we produced and examined a comprehensive list of all existing PeopleSoft user accounts, including those that were “locked.” PeopleSoft user data is cumulative, and old user accounts should not be deleted in order to avoid the risk of corrupting the integrity of historical data, according to current ITS practices. However, old user accounts for employees no longer requiring access to the system should be deactivated in accordance with GeorgiaFIRST Business Process Document SC.080.106 – “Managing Terminated User Access,” available online at the GeorgiaFIRST production Web site.
The risks of poor identity and access management are numerous:
- Increases the number of opportunities for inappropriate access to sensitive information contained within USG enterprise systems;
- Impacting institution security by failing to de-provision, deactivate and/or terminate unused accounts in a timely manner; and,
- Operational inefficiencies or introducing of information security risks due to misalignment or lack of communications between business areas.
As described by this document, all accounts for users no longer requiring access to the PeopleSoft system should first be “locked” from the User Profile screen, preventing the account from active use. However, an often overlooked second step is necessary to fully deactivate the account. Administrators should take the additional precaution of removing the “BOR PeopleSoft User” role from the account permissions on the User Roles page. Removing this role disallows the account from possessing sign-in credentials, thus preventing any future reactivation of the account. In our analysis, we found a substantial number of user accounts with no recorded activity for several years, which is to be expected – however, while most of these accounts were “locked,” many still possessed the “BOR PeopleSoft User” role permission.
Posted by Ted Beck
Published in: Audit Findings
Most Recent in: Audit Findings
5 Most Common External Audit Issues - FY2011
Posted by Ted Beck
October 25, 2012
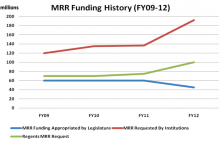
Use of Major Repair and Renovation Funds
Posted by Ted Beck
August 08, 2011

Financial Aid Purge Protections
Posted by Ted Beck
August 02, 2011
View Articles by Category
Search
Contact
Internal Audit & Compliance
Board of Regents of the University System of Georgia
270 Washington Street, SW
Atlanta, GA 30334
Tel.: 404-962-3020
Fax: 404-962-3033
Email: .(JavaScript must be enabled to view this email address)

