(Last Modified on June 18, 2021)
In March 2019, the content on Data Governance and Management has been moved from the USG Information Technology Handbook to the Business Procedures Manual. Compliance with this entire section is required for all USG organizations by December 31, 2023.
Due to the criticality of some sections and dependencies between them, compliance deadlines for the sections have been tiered. University System Office (USO) staff will be working with the appointed campus representative to track implementation.
Phase I - Initial Publication
Tier 1: Due by December 31, 2020, except General Data Protection Regulation, which is now part of Phase II, Tier 2.
- Section 12.3.1 Data System Documentation,
- Section 12.4 Cybersecurity (including Safeguards, Classification, Access Procedures and Segregation and Separation of Duties)
- Section 12.5.1 Regulatory Compliance.
Tier 2: Due by December 31, 2020
- Section 12.2 Governance Structure
- Section 12.3.4 Data Availability
- Section 12.5.2 Training
Tier 3: Due by June 30, 2021, except adherence to the USG document retention schedule, which should already be in place
- Section 12.3.2 Data Elements and Data Definition Documentation
- Section 12.3.3 Data Quality Control
- Section 12.3.5 Data Life Cycle
- Section 12.5.4 Monitor
- Section 12.5.4 Audit
Phase II - Addition of Section 12.6 Data Privacy
Tier 1: Due by December 31, 2022
- Section 12.6.4 Disassociation and De-identification
- Section 12.6.5 Data Processing Awareness
- Section 12.6.6 Communication
Tier 2: Due by December 31, 2023
- Section 12.6.1 Data Inventory
- Section 12.6.2 Data Risk Management
- Section 12.6.3 Data Processing Documentation
Information is a strategic asset of all University System of Georgia (USG) organizations and is critical to administration, planning and decision-making. Effective and responsible use of information requires that data is secure, well documented and accessible for use by authorized, trained personnel. To that end, this section of the Business Procedures Manual provides the data governance infrastructure and management practices that USG organizations must have in place. Please note that these different components have interdependencies and should be considered as a whole.
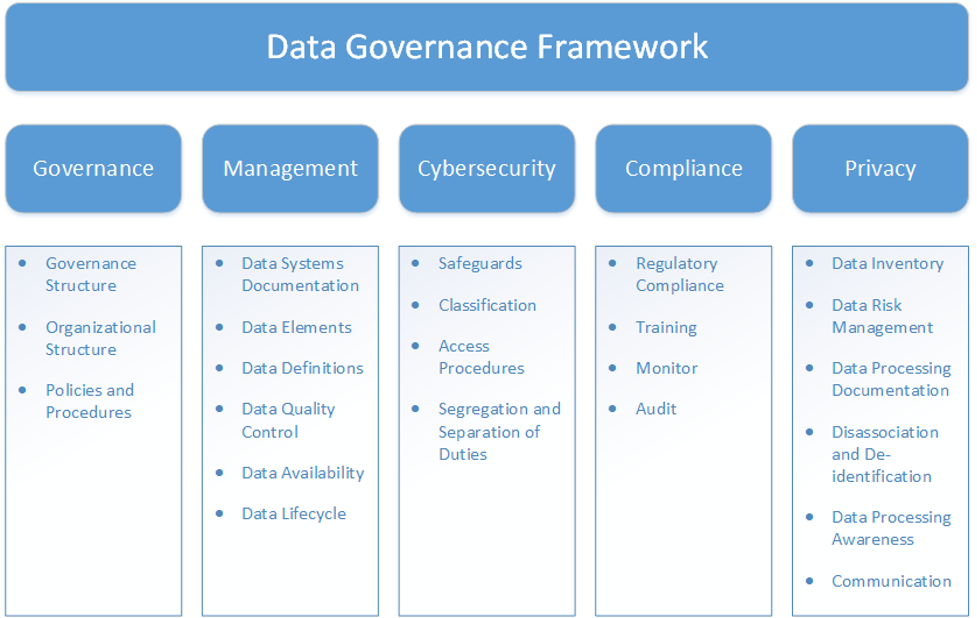
The goal of this section is to provide guidance to USG organizations in meeting the fundamental requirements for data governance and management to ensure data security, data privacy, effective use and compliance with relevant laws and policies. Technical requirements can be found in the USG IT Handbook. USG organizations may include additional roles, responsibilities, policies, and protocols as needed to fit local context or promote best practices. These provisions apply to information systems, products, and services maintained by, or on behalf of, USG organizations.
(Last Modified on August 26, 2021)
This section provides definitions needed to interpret the remainder of Section 12 content.
Attribute Reference is a statement asserting a property of an individual without necessarily containing identity information. For example, the attribute “birthday,” a reference could be “older than 18” or “born in December.”
Attribute Value is a statement asserting a property of an individual. For Example, the attribute “birthday,” a value could be “12/01/1980” or “December 1, 1980.”
Incident is a violation or imminent threat of violation of computer security or data privacy policies, acceptable use policies, or standard computer or privacy security practices.
Data Actions are system, product, or service data life cycle operations, including, but not limited to collection, retention, logging, generation, transformation, use, disclosure, sharing, transmission, and disposal.
Data Domains are high-level categories of Institutional Data for the purpose of assigning accountability and responsibility for the data.
Data Processing (“Processing”) refers to the collective set of data actions.
Data Processing Ecosystem is the relationship and dependency shared between groups of people involved in creating or deploying systems, products or services or any components that process data.
Data Subject is any person whose personal data is being collected, processed, or stored.
De-identification is the process used to prevent an individual’s (Data Subject) personal identity from being revealed. For example, data produced during human subject research might be de-identified to preserve privacy for research participants.
Disassociability is enabling the processing of data or events without association to individuals or devices beyond the operational requirements of the system.
Events, within the context of cybersecurity and data privacy, are questionable or suspicious activities that could threaten the security objectives concerning protected systems or data.
Information Systems (“Systems”) are the technology structure and software that carry out data processing.
Linkability is a possibility of logical association with other information about the individual.
Mission-Critical Systems are systems whose failure or malfunction will result in not achieving organizational goals and objectives. Criteria are a) contains confidential or sensitive data (i.e., personally identifiable information (PII) and other regulated information), or b) serves a critical and necessary function for daily operations, or c) a combination of both protected data and critical function.
Organizations are all USG institutions and the University System Office (USO), which includes the Shared Services Center (SSC), the Georgia Public Library Service (GPLS), the Georgia Archives and the Georgia Film Academy.
Organizational Data (“Data”) are data by, or on behalf of, a USG organization. Organizational Data are information that record facts, statistics or information, which is processed by offices of the organization. Data may be stored electronically or physically. Organizational data may reside in an organizational information system or a third-party system.
Principle of Least Privilege describes privileges to information resources permitting access to only what is necessary for the users to successfully perform their job requirements and assigned tasks.
(Last Modified on August 26, 2021)
This section describes the roles and responsibilities that USG organizations must designate and document within their data governance structure.
A data governance structure is required at each USG organization. The data governance structure will demonstrate accountabilities for the data assets of the organization to ensure proper processing.
The data governance structure documentation should identify the offices/positions (including incumbent) responsible for fulfilling the roles defined herein.
12.2.1 Governance and Organizational Structure
(Last Modified on August 26, 2021)
Data Governance Committee
The Data Governance Committee is responsible for defining, implementing, and managing policies and procedures for data governance and data management functions. Specific responsibilities include, but are not necessarily limited to the following:
- Defining data management roles and responsibilities contained in this section and other policy and procedure documentation;
- Maintaining documentation pertaining to data governance and management policy and procedure in a centralized and accessible location for the participant organization’s staff;
- Identifying the Data Governance and Management Committee structure and membership;
- Ensuring that cybersecurity and data privacy control processes detailed in the Cybersecurity section are developed and operational;
- Defining communications to instill data privacy values (set forth in section 12.6) within system, product or service development and operations (i.e., privacy by design); and,
- Assisting the chairs of the functional and technical committees to ensure effectiveness.
Functional Data Governance Committees
Functional Data Governance Committees are responsible for collective decision making around substantive changes to organization data collection, maintenance, access, and use within their functional area. It is the role of the Functional Data Governance Committee to identify what the threshold is for decisions to require Committee consideration. At some organizations, e.g., smaller institutions, the global Data Governance Committee may also fulfill the roles of the Functional Data Governance Committee.
Technical Data Governance Committees
Technical Data Governance Committees are responsible for technical guidance to support the work of the other Data Governance Committees and for decision making about the feasibility of and methods for carrying out decisions of the Functional Data Governance Committees. At some organizations, e.g., smaller institutions, the technical data governance roles must still be fulfilled but organizationally may be embedded in other Data Governance Committees.
Data Owner
Each USG organization is responsible for all data processed by offices of the organization. As the chief executive officer, the president of the USG institution, the Chancellor of the USG, or the head of other USG organizations is identified as the data owner. The USG organization data owner has ultimate responsibility for submission of organizational data to the USO.
Data owners have the responsibility for the identification, appointment and accountability of data trustees. Data owners will inform the USG organization’s Data Governance Committee of their data trustee appointments including office, name and contact information of the incumbent.
Data Trustees
Data trustees, designated by the data owner, are executives of the USG organizations who have overall responsibility for the data processed in their data area(s). USG organization data trustees have overall responsibility for accuracy and timeliness of submission of data to the USO. These positions/offices would normally be cabinet-level positions reporting directly to the entity data owner.
Responsibilities of the data trustees include, but are not necessarily limited to:
- Ensuring that data accessed and used by units reporting to them is done so in ways consistent with the mission of the office and USG organization;
- Appointing data stewards within each functional area for which they are responsible. The data trustees will inform the USG organization’s Data Governance Committee of their data stewards’ appointments, including office, name and contact information of the incumbent;
- Participating as a member of the Data Governance Committee; and,
- Communicating unresolved concerns about data (such as data quality, cybersecurity, data privacy, access, etc.) to the data owner.
Data Stewards
Data stewards, designated by the data trustees, are personnel responsible for the data processed, and the technology used to do so if applicable, in their data area(s). Data stewards recommend policies to the data trustees and establish procedures and guidelines concerning the access to, completeness, accuracy, privacy, and integrity of the data for which they are responsible. Individually, data stewards act as advisors to the data trustees and have management responsibilities for data administration issues in their functional areas. Data stewards have responsibility for accuracy and timeliness of submission of data to the USG system office in their area. Depending on the size and complexity of a functional department/division, it may be necessary, and beneficial, for a designated data steward to identify associate data stewards to manage and implement the stewardship process.
Responsibilities of the data stewards include, but are not necessarily limited to:
- Developing standard definitions for data elements created and/or used within the functional unit. The data definition will extend to include metadata definitions as well as the root data element definition;
- Ensuring data quality standards are in place and met;
- Inventorying and identifying the data as unrestricted, sensitive or confidential, for functional data within their area(s) of supervision/direction and communicate it to those responsible for ensuring data is handled according to its appropriate classification; (See 12.4.2 Classification)
- Establishing authorization procedures with the USG organization’s Data Governance Committee and/or chief information officer (CIO) to facilitate appropriate data access as defined by institutional/office data policy and ensuring security for that data. Authorization documentation must be maintained;
- Working with the USG organization’s Data Governance Committee, identifying and resolving issues related to stewardship of data elements, when used individually or collectively, that cross multiple units or divisions. For example, the individual data element “Social Security Number” may have more than one data steward since it is collected or used in multiple systems.
- Participating as a member of the Functional Data Governance Committee(s) as appointed by the data trustee.
- Communicating concerns about data (such as data quality, security, access, etc.) to the data trustees.
Chief Information Officer (CIO)/Chief Information Security Officer (CISO)
Responsibilities of the CIO and CISO are to ensure that technical infrastructure is in place to support the data needs and assets, including availability, delivery, access, and security across their operational scope.
(Last Modified on March 21, 2019)
This section contains data management requirements for data system documentation, data elements and data definition documentation, data quality and data availability.
12.3.1 Data System Documentation
(Last Modified on June 9, 2021)
This subsection defines documentation about USG organization data systems. Documentation is required to ensure proper accounting of the organization’s data systems, the relationships among them, the architecture of the individual systems, and the data within them. This documentation also fosters proper use.
USG organizations must maintain a listing of mission-critical data systems along with information essential to the effective loading, maintenance, use of, as well as reporting from those systems. This should include at a minimum:
- Function and purpose of the system;
- Who the data trustee and steward responsible for the system are;
- Who administers the system from a technical perspective;
- Any methods being applied to sustain data quality;
- Any important relationships and/or dependencies in business practice and reporting between systems;
- Any special life cycle requirements;
- User and technical guidelines for proper use and reporting;
- Process flow diagram(s); and,
- Contingency documentation.
12.3.2 Data Elements and Data Definition Documentation
(Last Modified on August 26, 2021)
For all data systems, there must be a mechanism to access documentation of the system’s table structure and data elements. In addition, for systems that are part of routine data collection and reporting, data element dictionaries should be maintained that include:
- Data definitions;
- Metadata including data sources and cybersecurity classifications;
- Business practices where applicable;
- Any validations or quality checks applied against the elements;
- Change history; and,
- Valid values.
12.3.3 Data Quality Control
(Last Modified on March 21, 2019)
USG organizations must ensure that information is of the highest possible quality to facilitate effective decision-making. Data quality refers to the accuracy, timeliness, comparability, usability, completeness and relevance of data. Data quality requires USG organizations to appropriately collect, store, process and manage data, whether electronic or physical. As part of data governance, USG organizations must communicate, prioritize and practice data quality. Just as institutions maximize their financial resources and facility assets, USG organizations should invest in the quality of their data holdings.
For all data essential to operation and reporting, each USG organization should:
- Document and promulgate data standards and definitions to ensure accurate data entry or data creation;
- Assess collected data to ensure accuracy, completeness, and adherence to standards at a minimum on an annual basis; and,
- Regularly consult data users or stakeholders to ensure data usability and relevance.
12.3.4 Data Availability
(Last Modified on June 9, 2021)
This subsection details minimum requirements for USG organizations concerning the availability of data resources. Assets of the USG should be available commensurate with their operational importance. For all data domains and their respective data systems, the organization should document and socialize to data users the expectations and processes around the availability of each data resource including, but not limited to:
- The periods of time data is available;
- Expectations for “uptime” (percent of time data is available) if appropriate;
- Modes of access (types of devices, etc.) that are provided for;
- Communications plan, including planned and unplanned system downtime; and,
- Method for users to report an unexpected lack of availability of data or data systems.
12.3.5 Data Lifecycle
(Last Modified on June 9, 2021)
Organizations should ensure their data retention and destruction efforts comply with the USG Records Retention Schedules referenced at http://www.usg.edu/records_management/.
Where organizations decide to maintain data longer than indicated in the USG Records Retention Schedules, documented considerations must include justification for maintaining the data longer than required, compliance with other policies and regulations, and associated risks and costs.
(Last Modified on June 9, 2021)
Cybersecurity refers to preventative methods used to protect information and information systems, products and services from unauthorized access, compromise or attack. Cybersecurity requires an understanding of potential threats and utilizes strategies that include, for example, identity management, risk management and incident management.
12.4.1 Safeguards
(Last Modified on June 9, 2021)
Shared information is a powerful tool and loss or misuse can be costly, if not illegal. The purpose of this section is to ensure that cybersecurity safeguards are established, in place, effective and adhered to in order to reduce risk. This applies to all users of USG information resources.
Safeguards include the policies, procedures, requirements, and practices that are necessary for maintaining a secure environment for the storage and dissemination of information. The objective of USG organizations is to protect information from inadvertent or intentional damage as well as unauthorized disclosures or use. The benefits of safeguards include identification of fraud, security vulnerabilities, unforeseen threats and minimization of potential impacts. Other benefits include audit compliance, service level monitoring, performance measuring, limiting liability and capacity planning. The USG recognizes that cybersecurity:
- Is everyone’s responsibility;
- Is a cornerstone of maintaining public trust;
- Should be risk-based and cost-efficient;
- Should align with USG priorities, industry best practices and government requirements; and,
- Should be applied holistically, regardless of medium.
USG organizations must designate trained cybersecurity representatives whose role includes:
- Communicating cybersecurity policies to all employees and contractors; and,
- Reporting deviations from policies and procedures.
USG organizations must:
- Develop procedures and processes that support compliance with Board of Regents (BOR) and USG policies and procedures. Organizational procedures and processes may be more specific than BOR and USG policies and procedures but shall in no case be less than the minimum requirements; and,
- Develop strategic and operational control guidance of hardware, software and telecommunications facilities; and,
- Re-evaluate cybersecurity and data privacy risk on an ongoing basis and as key factors, including the organization’s business environment, governance, data processing and systems/products/services change.
USG organizations must develop reporting processes to support investigation of and response to suspicious activities and follow USG guidelines for reporting or investigating acts of suspected malfeasance that involve organizational data as noted in the BOR University System of Georgia Ethics Policy.
12.4.2 Classification
(Last Modified on August 26, 2021)
Because USG data must be given appropriate protection from unauthorized use, access, disclosure, modification, loss or deletion, each USG organization must classify each record. When classifying a collection of data, the most restrictive classification of any of the individual elements should be used based on the following classification structure or similar schema required by regulations governing specific data domains:
- Unrestricted/Public Information is information maintained by a USG organization that is not exempt from disclosure under the provisions of the Open Records Act or other applicable state or federal laws. Some level of control is required to prevent unauthorized modification or destruction of public information.
- Sensitive Information is information maintained by a USG organization that requires special precautions to protect from unauthorized use, access and disclosure guarding against improper information modification, loss or destruction. Sensitive information is not exempt from disclosure under the provisions of the Open Records Act or other applicable state or federal laws but is not necessarily intended for public consumption.
- Confidential Information is information maintained by a USG organization that is subject to authorized restrictions on information access and disclosure, including, without limitation, the protection of personal privacy and proprietary information. (44 USC Sec 3542) Confidential classified documents are exempt from disclosure under the provisions of the Open Records Act or other applicable state or federal laws.
Note: The Open Records Act is located at http://law.ga.gov/law.
In addition, Personal Information may occur in unrestricted/public, sensitive, and/or confidential information. It is information that identifies or describes an individual and must be considered in the classification structure. Please refer to the IT Handbook for further information and guidance. Information classification must be part of the information technology risk management program, as detailed in the IT Handbook.
12.4.3 Access Procedures
(Last Modified on August 26, 2021)
This section promotes secure and appropriate access to USG information systems, and to the data used, processed, stored, maintained and/or transmitted in and through those systems. It is essential that access to and use of the USG’s information systems and data are properly secured and protected against cybersecurity and data privacy threats and dangers.
All users are required to adhere to the following rules in order to process data acquired from USG information systems. These rules also apply to any contractors or non-USG persons who acquire access to USG systems in any format, and on any device.
Procedures:
USG organizations shall identify and categorize information systems that process or store confidential or sensitive information, or are critical systems. The suggested responsible party is the data trustee or designee.
USG organizations will identify the data trustee and data steward for each critical system or systems containing confidential or sensitive information. A list of these systems and the associated trustee and steward shall be made available upon request.
USG organizations will maintain a current list of users granted access to information systems. Only authorized users should be allowed physical, electronic or other access to information systems.
USG organizations will define both administrative and technical access controls. The suggested responsible parties are Human Resources (HR), the data trustee and data steward.
Access controls must include, but are not limited to:
- Documented procedures to grant, review, deactivate, update or terminate account access;
- Ensure appropriate resources are available and maintained to adequately authenticate and verify authorized access; and,
- Ensure appropriate resources are available and maintained to prevent and detect unauthorized use.
Data trustees, data stewards and users share the responsibility of preventing unauthorized access to USG organizations’ information systems.
Data stewards will analyze user roles and determine the level of access required to perform a job function. The level of authorized access must be based on Principle of Least Privilege.
HR and/or the supervisor will notify the data steward of personnel status changes in job function, status, transfers, referral privileges or affiliation.
Access to an information system must be reviewed regularly. Data stewards must review user access to the information system every six months and document findings.
Data trustee or designee will ensure that a business process exists to update information system access no more than five business days after terminations and no more than 30 days after other personnel status changes.
12.4.4 Segregation and Separation of Duties
(Last Modified on March 22, 2019)
In addition to having a well-organized and defined data governance structure, USG organizations must ensure that its organizational structure, job duties, and business processes include an adequate system of separation of duties (SOD) taking into account a cost-benefit and risk analysis. SOD is fundamental to reducing the risk of loss of confidentiality, integrity and availability of information. To accomplish SOD, duties are divided among different individuals to reduce the risk of error or inappropriate action. For example, the employee or office responsible for safeguarding an asset should be someone other than the employee or office that maintains accounting records for that asset. In general, responsibility for related transactions should be divided among employees so that one employee’s work serves as a check on the work of other employees. When duties are separated, there must be collusion between employees for assets/data to be used inappropriately without detection.
While electronic processes enhance accuracy and efficiency, they also can blur SOD. USG organizations must evaluate and establish well-documented controls to deter an individual or an office from having the authority (or the ability) to perform conflicting functions both outside and within technology information systems.
(Last Modified on June 4, 2021)
Meeting the provisions of Section 12 on Data Governance and Management requires active measures by USG organizations to ensure ongoing compliance. These include ensuring compliance with external regulations in addition to the provisions in this section through regular training, monitoring and auditing.
12.5.1 Regulatory Compliance
(Last Modified on September 23, 2021)
Closely managing data content is necessary to ensure compliance with federal, state and local regulations as well as grants and contract specifications. Each USG organization is responsible for clearly understanding and managing data and data privacy to ensure sensitive and confidential data is appropriately classified and safeguarded. Each USG organization must have policies and procedures to ensure that appropriate organizational personnel has a working knowledge of:
- Georgia’s Open Records Act OCGA § 50-18-70
- Family Education Rights and Privacy Act (FERPA)
- U.S. Department of Health and Human Services Health Information Portability and Accountability Act (HIPAA)
- Gramm-Leach-Bliley Act (GLBA)
- General Data Protection Regulation (GDPR)
- Specific research data requirements
- Other applicable regulations
12.5.2 Training
(Last Modified on June 9, 2021)
The purpose of this section is to ensure that appropriate individuals at each USG organization receive training on the data governance policies, procedures, and roles developed in compliance with preceding requirements in this Data Governance and Management section.
Organizations must:
- Provide role specific training to all individuals within the data governance structure, including data users and all those subject to data governance policies;
- Ensure individuals understand their roles and the larger governance structure, responsibilities, and applicable policies and procedures;
- Provide training to individuals as they enter these roles, when there are substantive changes to training and at regular intervals over time to ensure up-to-date understanding;
- Update training materials as changes to policy and procedure require;
- Document participation in training and audit training participation at regular intervals;
- Provide training materials in a permanent form (such as on a website) for individuals to reference as needed;
- Specifically address in training materials for all individuals how data classified as public or protected is managed throughout its lifecycle; and,
- Provide clear information about how an individual should proceed if he or she believes data policies or standards (including those regarding data management, cybersecurity and privacy) are not followed, or there has been a breach of data security.
12.5.3 Monitor
(Last Modified on June 9, 2021)
Each USG organization’s Data Governance Committee is responsible for assigning roles and responsibilities for data governance and management per Section 12.2.1. In addition to ensuring cybersecurity and data privacy compliance, organizations must assign roles and responsibilities for active monitoring and communicating the results of these efforts.
12.5.4 Audit
(Last Modified on March 22, 2019)
Compliance with this Data Governance and Management section of the BPM can be a subject of institution, system or state audit. Institutions must maintain records not only of documentation explicitly referenced in this section but also general evidence that the organization is in compliance with its data governance and management policies and procedures.
(Last Modified on June 4, 2021)
The USG is committed to protecting privacy. Personal information will only be disclosed to third parties when allowed by law or with the consent of the data subject.
USG provides additional data privacy compliance guidance at /policies/dataprivacy.
12.6.1 Data Inventory
(Last Modified on August 26, 2021)
Compliance due by December 31, 2023
See supporting RoPA Process Guide at /policies/dataprivacy.
Processing of organizational data by systems, products or services must be understood and used to inform management of privacy risk. Inventorying data is a foundational step in identifying the assets that are to be protected. Organizations must:
- Inventory systems, products or services managing individuals’ (data subjects) data;
- Inventory the data actions of the systems, products or services managing data; and,
- Inventory the purposes for the data actions managing data.
12.6.2 Data Risk Management
(Last Modified on August 26, 2021)
Compliance due by December 31, 2023
See supporting RoPA Process Guide at /policies/dataprivacy.
Establishing priorities, constraints, risk tolerance, and assumptions are the next steps to support risk decisions associated with managing privacy risk and third parties. Organizations shall confirm:
- All parties in the data processing ecosystem are identified, assessed and prioritized to support operational risk decisions; and,
- Contracts or multi-party approaches are used to achieve data privacy objectives and manage data privacy risks.
12.6.3 Data Processing Documentation
(Last Modified on August 26, 2021)
Compliance due by December 31, 2023
See supporting RoPA Process Guide at /policies/dataprivacy.
For data systems determined in the inventory to contain personal information (Section 12.6.1), it is essential that written documentation is used to manage data processing to protect individuals (data subjects) and reduce organizational risk. Organizations must document both their policies, processes and procedures regarding, and execution of:
- Authorizing data processing, revoking authorizations and maintaining authorizations; and,
- Enabling individuals’ data processing preferences and requests that are required by law/policy.
12.6.4 Disassociation and De-identification
(Last Modified on June 4, 2021)
Compliance due by December 31, 2022
See supporting DSR Process Guide at /policies/dataprivacy.
As an objective of data privacy, data processing solutions shall increase disassociability to protect individuals’ (data subject’s) privacy and enable implementation of privacy principles (e.g., data minimization). Organizations must process privacy protected data to limit to the extent possible:
- Observability and linkability (e.g., encryption);
- Identification of individuals;
- Formulation of inferences about individuals’ behavior or activities;
- Collection or disclosure of data elements; and,
- Attribute values, substitute with attribute references.
12.6.5 Data Processing Awareness
(Last Modified on August 26, 2021)
Compliance due by December 31, 2022
See supporting DSR Process Guide at /policies/dataprivacy.
Awareness of data processing practices and associated privacy risks must be shared with individual (data subject) and organizational stakeholders. To support awareness, organizations must:
- Implement mechanisms (e.g., notices, internal or public reports) for communicating data processing purposes, practices, associated privacy risks and options for enabling individual’s (data subject’s) preferences and requests where allowable by law;
- Maintain records of unintended data disclosures to be accessed for investigative review;
- Develop and implement policies and processes for receiving, tracking and responding to complaints, concerns and questions from individuals about organizational privacy practices;
- Communicate requested data corrections or deletions to individuals (data subjects) or organizations making such requests;
- Notify impacted individuals (data subjects) and/or organizations as required by law concerning a privacy breach or event; and,
- Provide individuals (data subjects) with mitigation mechanisms as required by law to address impacts of a privacy breach or event.
12.6.6 Communication
(Last Modified on June 4, 2021)
Compliance due by December 31, 2022
See supporting DSR Process Guide at /policies/dataprivacy.
Beyond awareness, communication must be employed to increase transparency of the organization’s data processing practices and associated privacy risks. Organizations shall promote communications through written policies, processes and procedures that include:
- Establishing roles and responsibilities (e.g., public relations) for communicating data processing purposes, practices and associated privacy risks to external stakeholders; and,
- Communicating data processing purposes, practices and associated privacy values, policies and risks.
↑ Top
